PSA: With over 40 million users, Steam is likely an attractive target for hackers, but very few cases of malware have occurred on the storefront over its two-decade history. Although a recent incident isn’t as severe as last month’s, it suggests that scammers are stepping up their efforts to bypass Valve’s security measures.
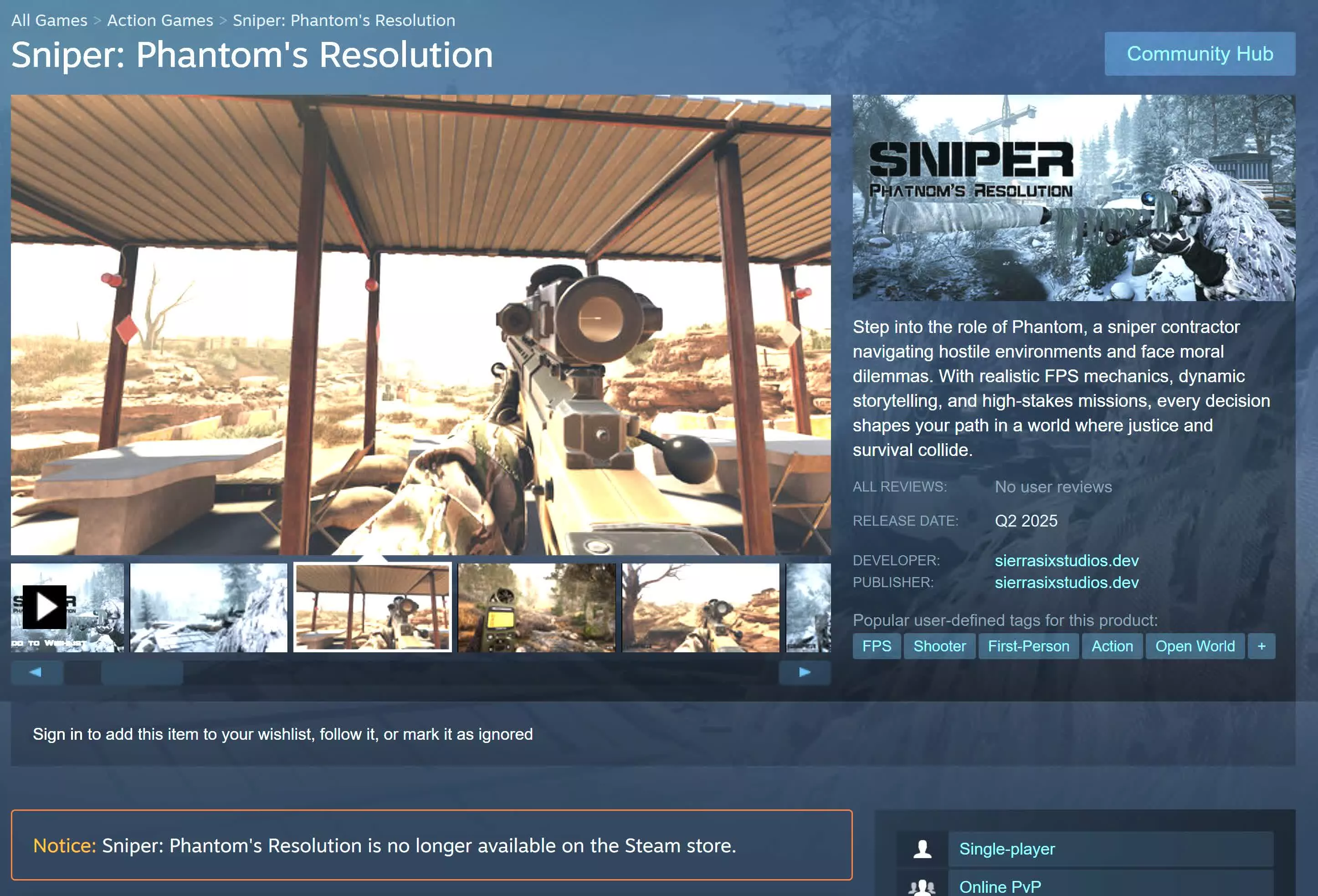
Users who downloaded a demo for the game Sniper: Phantom’s Resolution should immediately delete all associated files and change their passwords. The game was removed from Valve’s platform after users discovered its store page linked to an info-stealer.
Despite Steam’s relatively lenient content policies, users have rarely suspected the client itself of distributing malware. The fraudulent free-to-play game PirateFi, discovered last month, was possibly the first well-known case of its kind since Steam’s debut as the installer for Half-Life 2 in 2004. The latest example attempted to evade Valve’s security by hosting a free demo on a separate website.
Although it isn’t unheard of for Steam games to host downloads outside the client, users should take extreme caution when clicking links leading to external websites. Valve’s warnings regarding outward links may seem annoying, but they’re there for a reason.
Redditor “Feral_Wasp” first reported Phantom’s Resolution after noticing multiple red flags. Aside from the external free demo and generic production art, they had first heard about the game through an unsolicited direct message on Discord – an approach commonly used by scammers.
Further investigation revealed that the developer’s website was registered earlier this month, and the images associated with their accounts might have been stolen. They may also be linked to a crypto enterprise and appear to be promoting the game via Telegram, the same messaging service used in the PirateFi scam.
After testing the “demo” in a virtual machine, another user discovered files designed to evade Windows Defender, mimic the Unity engine, escalate privileges, and run Fiddler – a known network traffic interceptor. VirusTotal struggles to detect the malware, suggesting it is either new or custom-built. Windows Defender, however, flags it as a trojan.
Although the Steam page’s external link directed users to an independent website presumably run by the developer, the malicious payload actually originated from the group’s GitHub repository. Unlike the PirateFi incident, Valve has not yet issued warning emails to affected users. However, Steam has marked the game as unavailable, and GitHub appears to have taken down the developer’s page after users reported it.